ThreatSentry 4
 ThreatSentry Windows Web server Host Intrusion Prevention software defends IIS against new and progressive attack techniques, protects network weak points, overcomes lapses in patch management, and reinforces regulatory compliance.
ThreatSentry Windows Web server Host Intrusion Prevention software defends IIS against new and progressive attack techniques, protects network weak points, overcomes lapses in patch management, and reinforces regulatory compliance.
|
ThreatSentry Windows Web server Host Intrusion Prevention software defends IIS against new and progressive attack techniques, protects network weak points, overcomes lapses in patch management, and reinforces regulatory compliance.
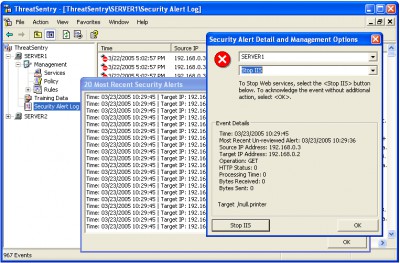
An ISAPI filter hosted in MMC, ThreatSentry compares server requests to a knowledgebase and an evolving system baseline to detect untrusted activity and prevent attacks on Microsoft IIS. Supports Win 2/2003, IIS 5/6.
Unsurpassed Protection from Known/New, Internal/External Threats -
Advanced system/behavior profiling and comparative analysis engine enables ThreatSentry to extend the intrusion detection and prevention capabilities of conventional pattern matching, rules, and policy-based systems.
ThreatSentry is invaluable in protecting IIS servers from an array of vulnerabilities including Directory Traversal, Parameter Manipulation, Buffer Overflow, Parser Evasion, High-bit Shellcode, Printer Protocol, Remote Data Services, and others. Alerts, IP blocking and other preventative mechanisms can be activated on demand or pre-configured based on corporate security policies.
Unparalleled Affordability and Ease-of-Use - ThreatSentry is an IIS ISAPI filter and Snaps-in to the Microsoft Management Console (MMC). It is exceptionally easy to use and affordably priced for enterprises of any size.
ThreatSentry features
The integrated firewall can block all network ports for IPs listed in the Blocked List.
Requirements
IIS 5.0 or Higher Installed
tags![]() event details isapi filter
event details isapi filter
Download ThreatSentry 4
Purchase: ![]() Buy ThreatSentry 4
Buy ThreatSentry 4
Similar software
 ThreatSentry 4
ThreatSentry 4
Privacyware
ThreatSentry Windows Web server Host Intrusion Prevention software defends IIS against new and progressive attack techniques, protects network weak points, overcomes lapses in patch management, and reinforces regulatory compliance.
 Privatefirewall 7.0.24.10
Privatefirewall 7.0.24.10
PWI, Inc
Privatefirewall is an integrated desktop firewall and multi-layer intrusion prevention software delivers signature-less, zero-hour protection from known or new spyware, viruses, hacking techniques and other intrusions on Windows desktops and servers.
 GFI LANguard Security Event Log Monitor 5
GFI LANguard Security Event Log Monitor 5
GFI Software
LANguard Security Event Log Monitor is a network wide event log monitor that retrieves logs from all NT/2000 servers and workstations and immediately alerts the administrator of possible intrusions for immediate host based intrusion detection.
 Security Center Lite 1.3.2
Security Center Lite 1.3.2
Lan-Secure
Security Center is an intrusion detection and prevention product.
 WehnTrust 1.0.0.9
WehnTrust 1.0.0.9
Wehnus
WehnTrust is a useful Host-based Intrusion Prevention System (HIPS) which provides secure buffer overflow exploitation countermeasures.
 Logalot 3.0
Logalot 3.0
Somix Technologies Inc
Somix is a leader in Security Information Management and Intrusion Protection.
 ALLESTA 1.3
ALLESTA 1.3
BuyServers Ltd.
Allesta Web Application Firewall provides a proactive application level protection through instant detection and prevention of attacks.
 Security Center Pro 1.3.2
Security Center Pro 1.3.2
Lan-Secure
Security Center is a security application that monitors network traffic and protects you from potential intruders.
 AntiHook 3.0.0.23
AntiHook 3.0.0.23
InfoProcess
AntiHook is the ultimate host intrusion prevention system for protection against malicious software.
 Panda TruPrevent Corporate 3.06
Panda TruPrevent Corporate 3.06
Panda Software
Panda TruPrevent Corporate 2006 is the most effective solution for protecting your corporate network against unknown viruses and threats, acting as the perfect complement to your current antivirus solution
· Secure communications
In order to intercept hackers and intruders, TruPrevent Corporate 2006 monitors communications and the memory: it prevents buffer overflows and exhaustively scans communication packets transmitted with an automatic firewall in order to detect techniques such as attempts to identify the operating system, port scanning, denial of service attacks (DoS), IP Spoofing, MAC Spoofing.