Iside 4.2.1020
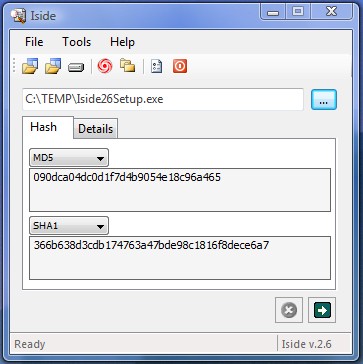
 Iside compares files and folders by computing their hash code (MD5,SHA1,CRC32,.
Iside compares files and folders by computing their hash code (MD5,SHA1,CRC32,.
|
Iside compares files and folders by computing their hash code (MD5,SHA1,CRC32,...). Right click on a file, select Copy and by right clicking on another file you will discover if the two files are equal. Includes file comparison, hash generating tool plus a complete folder comparison tool.
The hash function is the fingerprint of file. It allows to determine if two files are different even if their size is the same. Ideal tool for configuration managers, programmers, deployers.
Iside is a software that allows you compare files.
Useful also to compare photos, music and movies downloaded from Internet. It can also be used for file integrity checking.
Requirements
Requires Microsoft .NET Framework v.1.1
Limitations
Download Iside 4.2.1020
Purchase: ![]() Buy Iside 4.2.1020
Buy Iside 4.2.1020
Similar software
 Iside 4.2.1020
Iside 4.2.1020
LittleLite Software
Iside compares files and folders by computing their hash code (MD5,SHA1,CRC32,.
 HashPuff 1.0.3
HashPuff 1.0.3
Occam Technologies
HashPuff is a useful and reliable file comparison tool.
 Gizmo Hasher 2.0.4
Gizmo Hasher 2.0.4
Arainia Solutions
Gizmo Hasher is a useful program that lets you to calculate hash values (a.
 MD5 Fingerprint 1.2
MD5 Fingerprint 1.2
Ricardo Amaral
MD5 Fingerprint is a simple software application that you can use to calculate the MD5 hash for any file, and then compare it to another one.
 File Compare XP 1.0
File Compare XP 1.0
eXcessive Software
File Compare XP is a small application that compares two files.
 febooti fileTweak Hash & CRC 2.0
febooti fileTweak Hash & CRC 2.0
Febooti Software
febooti fileTweak Hash & CRC is a free and useful hash / CRC calculator.
 Compare PDF 3.0
Compare PDF 3.0
AKS-Labs
Compare PDF can compare both - related and non-related files.
 Hyper Hasher Suite 6.0.4
Hyper Hasher Suite 6.0.4
Matt LaPlante
Hyper Hasher is a small utility that allows you to calculate hash/checksum values for any file on your system, or text string.
 HashCalc 2.02
HashCalc 2.02
SlavaSoft Inc
Free calculator to compute multiple hashes, checksums and HMACs for files, text and hex strings.
 Pinpoint Hash 1.0.0
Pinpoint Hash 1.0.0
Pinpoint Laboratories
Forensic examiners often need to quickly obtain the hash values for potential evidence files for reports or to verify their results.