Invisible Secrets 4.7
 Invisible Secrets not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages.
Invisible Secrets not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages.
|
Invisible Secrets not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages.
These types of files are a perfect disguise for sensitive information. Nobody, not even your wife, boss, or a hacker would realize that your important papers or letters are stored in your last holiday pictures, or that you use your personal web page to exchange messages or secret documents.
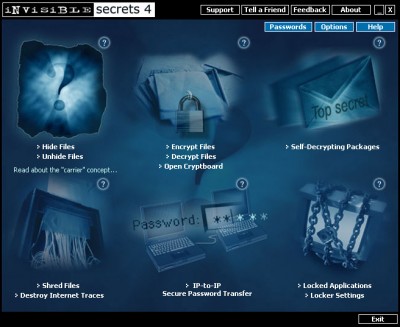
Invisible Secrets features: strong encryption algorithms; a password management solution that stores all your passwords securely and helps you create secure passwords; a shredder that helps you destroy beyond recovery files, folders and internet traces; a locker that allows you to password protect certain applications; the ability to create self-decrypting packages and mail them to your friends or business partners; a tool that allows you to transfer a password securely over the internet and a cryptboard to help you use the program from Windows Explorer.
Invisible Secrets is shell integrated and offers a wizard that guides you through all the necessary steps needed to protect your data .
Invisible Secrets features
tags![]() invisible secrets the internet self decrypting the program all the the process source data create self allows you you use your data secrets features helps you
invisible secrets the internet self decrypting the program all the the process source data create self allows you you use your data secrets features helps you
Download Invisible Secrets 4.7
![]() Download Invisible Secrets 4.7
Download Invisible Secrets 4.7
Purchase: ![]() Buy Invisible Secrets 4.7
Buy Invisible Secrets 4.7
Similar software
 Invisible Secrets 4.7
Invisible Secrets 4.7
Neobyte Solutions
Invisible Secrets not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages.
 Steganography 1.8.1.1001
Steganography 1.8.1.1001
SecureKit Inc
Steganography is your boss spying your outside and inside emails?
Is your wife or husband surveying your letters from other friends?
Are you afraid that your competitors in company or in business penetrate your system and find your valuable information?
Data transmissions are vital and became a necessity nowadays.
 Another ViewPoint 5.01
Another ViewPoint 5.01
janusware
Everybody has a right to privacy and business secrets.
 Password Manager XP 4.0.804
Password Manager XP 4.0.804
CP-Lab
Password Manager XP is a program that helps you to systematize any secret information stored on your PC.
 PowerKey 2.0
PowerKey 2.0
Elcor Software
PowerKey offers you an advanced encryption toolkit to protect sensitive and important data on your system.
 Masker 1.9
Masker 1.9
SoftPuls.com
Masker is a useful program that can hide folders and files, protect and encrypt!
Masker is a program that encrypts your files so that a password is needed to open them, and then it hides your files within other files known as carrier files.
 File Secret 1.0
File Secret 1.0
Ideas Infotech
File Secret is a Unique Collection of File Base utility for Hiding, Protecting, Locking and safely destroying a File.
 Absolute Password Protector 1.0.547
Absolute Password Protector 1.0.547
LastBit Software
Absolute Password Protector is a strong encryption utility that securely encrypts files.
 Max File Encryption 2.0
Max File Encryption 2.0
Softeza Development
When sending sensitive information via e-mail, you assume the risk that your info might be intercepted.
 Secrets Viewer 1.1
Secrets Viewer 1.1
Igor Tolmachev
Secrets Viewer is a small tool that retrieves the passwords stored on your computer by Internet Explorer, Outlook Express and MSN Explorer.