CryptoForge 5.5.0
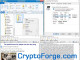 CryptoForge is a suite of encryption tools for personal and professional security.
CryptoForge is a suite of encryption tools for personal and professional security.
|
CryptoForge is a suite of encryption tools for personal and professional security. It allows you to protect the privacy of your sensitive files and messages by encrypting them with up to four strong cryptographic algorithms. Once the information has been encrypted, it can be stored on insecure media or transmitted on an insecure network -like the Internet, and still remain secret.
Later, the information can be decrypted into its original form. It enables you to encrypt, decrypt, and wipe -with the built-in file shredder files of any type, as well as entire folders and drives, from within Windows Explorer or My Computer with right-click ease.
An included secure text editor allows you to create, encrypt, and decrypt documents in a way that can be sent through any email, messenger, or chat program.
CryptoForge uses four strong (symmetric) cryptographic algorithms to protect your information:
Blowfish (448-bit key) is a strong and fast algorithm designed by Bruce Schneier, one of the most prestigious cryptographers all over the world.
Rijndael (256-bit key) is a high security algorithm created by Joan Daemen and Vincent Rijmen (Belgium). Rijndael is the new Advanced Encryption Standard (AES) chosen by the National Institute of Standards and Technology (NIST).
Triple DES (168-bit key) is a strong, well-known, U.S. Government algorithm. TripleDES use the DES algorithm three times with three different keys.
Gost (256-bit key) is a cryptographic algorithm from Russia that appears to be the Russian analog to DES. Gost has undergone intensive peer review and is regarded to be secure.
At present, there is no way to break any of these algorithms, unless to try all possible keys. If one billion computers were each searching one billion keys per second, it would take over 10*10ˆ24 years to recover information encrypted with a 168-bit algorithm (the age of the universe is 10*10ˆ9 years). In addition, CryptoForge implements mechanisms against modifications in its code. When executed, it verifies the algorithms with the test vectors provided by their designers.
The four algorithms implemented in CryptoForge are Block Ciphers. This means that they encrypt data in block units, rather than a single bit at a time. The algorithms are used in Cipher Block Chaining mode, where the original data is XORed with the previous ciphertext before encryption. On the first encryption, a random-generated 128-bit Initialization Vector is used as the ciphertext. CBC mode ensures that even if the data contains many identical blocks, they will each encrypt to a different ciphertext block.
When you enter your passphrase into CryptoForge, it is hashed with a Hash algorithm to generate a fingerprint, also known as digest. The one-way Hash function takes variable-length input, in this case your passphrase, and produces a fixed-length output. Also ensures that, if the passphrase is changed -even by just one bit- an entirely different output value is generated. This value is the key actually used by the cipher. That process is repeated using a different Hash function for each encryption algorithm, thus generating four unique keys.
Although CryptoForge allows encryption with more than one algorithm, for most users this might be considered unnecessary, because the level of protection provided by any of the employed algorithms is (at least in the unclassified world), good enough. However, this ensures that even if in the future one of them is attacked, your information will remain protected. Actually, it is surprisingly difficult to determine just how good an encryption algorithm is. If you wish to use more than one encryption algorithm, changing the order in which they are used should add another problem to a hardware-based attack (i.e. an array of special chips trying trillions keys a second).
Secure file deletion is accomplished by writing a pattern of all ones, zeros, and a stream of pseudo- random data, iterating the number of times specified by the user. The name of the file is overwritten as well. The length of the file is then truncated to zero.
tags![]() bit key ensures that with the encryption algorithm that even the file your passphrase hash function are used than one more than one billion the information
bit key ensures that with the encryption algorithm that even the file your passphrase hash function are used than one more than one billion the information
Download CryptoForge 5.5.0
Purchase: ![]() Buy CryptoForge 5.5.0
Buy CryptoForge 5.5.0
Similar software
 CryptoForge 5.5.0
CryptoForge 5.5.0
Ranquel Technologies
CryptoForge is a suite of encryption tools for personal and professional security.
 PrimaSoft Encryption - Service Edition 1.0
PrimaSoft Encryption - Service Edition 1.0
PrimaSoft PC Inc
PrimaSoft Encryption is a Windows program which allows you quickly and easely to run scheduled encryption and decryption sessions as a service process using the latest industry standard strong encryption algorithms: AES (US Advanced Encryption Standard, secret-key encryption also known as Rijndael); Twofish (secret-key encryption); RSA (public-key encryption)
Features:
· Encryption software: service process: You can run scheduled auto-recurring encryption and decryption sessions as a service process.
 HsCipherSDK Encryption Library 2.2
HsCipherSDK Encryption Library 2.2
Hillstone Software
HsCipherSDK is an Encryption Library that provides an API to a suite of symmetric key cryptographic algorithms and one way hash digital signature algorithms.
 DevSolutions Crypt 1.0.1
DevSolutions Crypt 1.0.1
DevSolutions
DevSolutionsCrypt library is a powerful and easy to use cryptographic ActiveX and DLL component for Windows developers that allows applications to encrypt/decrypt data or files using the latest industry standard strong encryption algorithms.
 BCArchive 2.06.4
BCArchive 2.06.4
Jetico, Inc.
BCArchive software you may encrypt and compress a group of files/folders
to an encrypted archive (i.
 Xceed Encryption Library 1.1
Xceed Encryption Library 1.1
Xceed Software Inc.
Xceed Encryption Library is an ActiveX component that allows Windows applications to encrypt and decrypt data using the latest industry standard strong encryption algorithms.
 JumBlo 1.3
JumBlo 1.3
Siskin
JumBlo came up for those who are in need to transfer in a secure way sensitive data between Siskin headquarters and various project sites.
 CipherWall Self-Decryptor 2.42 Build 1011
CipherWall Self-Decryptor 2.42 Build 1011
Vsevolod Yevgiyenko
CipherWall Self-Decryptor is a program designed for self-decrypting archives creation and data wiping.
 Smart Encryptor - Encryption Manager 4.2
Smart Encryptor - Encryption Manager 4.2
Smart Soft
SmartEncryptor uses the most powerfull encryption algorythms existing.
 CryptoFish 1.1
CryptoFish 1.1
Jan Dolinay
CryptoFish is encryption utility that you can use to encrypt/decrypt files and folders to protect them from unauthorized use.