Computer Security 1.5
 Security should be a very important and concerning issue in you every day activity.
Security should be a very important and concerning issue in you every day activity.
|
Security should be a very important and concerning issue in you every day activity. No matter you are part of a company or a home user, it is very important to protect your files.
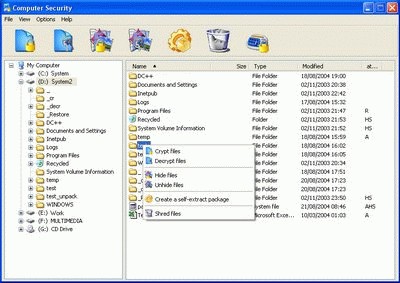
Computer Security does that for you encrypting sensitive data, hiding it in innocent carriers, allowing safe transfer through encrypted self-extract package, deleting files beyond recovery and locking application from your children or " welcomed quests".
Encryption is done using one of over 20 algorithms like Twofish, Cast128, Blowfish or Shaphire II. A special algorithm is used for secure erase that overwrites every bit of information with a random number of layers of data.
Download Computer Security 1.5
![]() Download Computer Security 1.5
Download Computer Security 1.5
Purchase: ![]() Buy Computer Security 1.5
Buy Computer Security 1.5
Similar software
 Computer Security 1.5
Computer Security 1.5
Adolix
Security should be a very important and concerning issue in you every day activity.
 Invisible Secrets 4.7
Invisible Secrets 4.7
Neobyte Solutions
Invisible Secrets not only encrypts your data and files for safe keeping or for secure transfer across the net, it also hides them in places that on the surface appear totally innocent, such as picture or sound files, or web pages.
 ID Data Encrypt 1.2
ID Data Encrypt 1.2
ID Security Suite
ID Data Encrypt is a high-priority security program, responsible for your computer’s real-time protection against hackers.
 SafeBit 1.5
SafeBit 1.5
NeoByte Solutions
SafeBit is the perfect electronic vault you need for your privacy.
 Cipherlok 2.1
Cipherlok 2.1
Softlok International Ltd
Cipherlok is a data security product that provides easy to use yet highly secure encryption of files on your PC or notebook using the Blowfish algorithm.
 JumBlo 1.3
JumBlo 1.3
Siskin
JumBlo came up for those who are in need to transfer in a secure way sensitive data between Siskin headquarters and various project sites.
 Advanced Encryption Plug-In Pro for Windows Explorer 4.0.5
Advanced Encryption Plug-In Pro for Windows Explorer 4.0.5
SecureAction Research LLC
AEPE lets you encrypt files using 17 encryption algorithms and also shred/make encrypted .
 StealthDisk 2004.1.909
StealthDisk 2004.1.909
Security Group Six
Using up to 448-bit encryption.
 CryptoWorks 1.0
CryptoWorks 1.0
Slazetech
CryptoWorks is a useful encryption utility, which allows you to encrypt and decrypt files.
 TigerCrypt 3.2
TigerCrypt 3.2
kaiwitte.org
TigerCrypt is a application to encrypt / decrypt files.