BestCrypt Corporate 1.12
 BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
BestCrypt Corporate includes standard BestCrypt software that performs encryption/decryption operations creating virtual drives acting as regular drives.
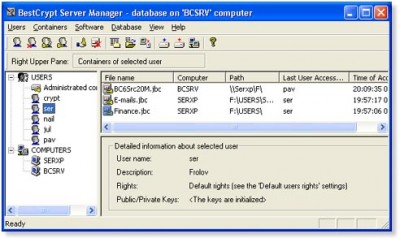
The core of BestCrypt Corporate is BestCrypt Central Manager that provides all range of functions: automatic installation/uninstallation and update of BestCrypt on remote client computers, creation of central Administrating Database on the server.
Central Administrating Database keeps tracks of all passwords used by client computers to create containers to keep data inside in encrypted form.
Secret data kept on client computers can be always accessed by Administrator, even if employee is away or gone.
Central Administrating Database can be also scheduled for automatic backup. BestCrypt Corporate is important tool to keep corporate networks secure and at the same time, it provides easy yet powerful way to manage secret data in networks consisting from 5 to 100 000 computers.
The BestCrypt software performs encryption using the strongest algorithms available including:
The Rijndael (AES) algorithm in Cipher Block Chaining mode
Russian Federal Standard GOST 28147-89 in Cipher Feedback mode
Blowfish in Cipher Block Chaining mode
Twofish in Cipher Block Chaining mode
BestCrypt Corporate features
1. Our new product BestCrypt Corporate Edition is specifically designed to satisfy every need of the corporate environment. BestCrypt Corporate Edition enables Windows NT/2000/XP Domain Administrators to remotely control all the functionality of BestCrypt software on any number of computers (including automatic installation and upgrading of client software and remote key management).
2. BestCrypt v.7 is fully compatible with Windows XP. Now encrypted virtual drives get additional support from standard Windows 2000 / Windows XP disk levels, as it can be seen from "Disk drives -> BestCrypt virtual drive" properties in Windows 2000/XP Device Manager after mounting BestCrypt drive.
3. Swap File Encryption utility is now included in BestCrypt software, version 7. The Swap File is a Windows system file that is used for virtual memory support. It can store portions of documents, that you were or are working with, in an opened form on the hard drive. Even if you have used a powerful program to encrypt one of your original documents, Windows can copy that document in whole or in part to the Swap file in decrypted form. Encryption keys, passwords, and other sensitive information can also be swapped to the hard drive. Even if you use all of the security features provided in the latest version of Windows, a simple investigation of the Swap file in DOS mode using readily available tools will give an intruder access to your most sensitive information. To the best of our knowledge, only BestCrypt v.7 can prevent such an attack on your data by allowing you to encrypt the contents of your Swap file.
4. BestCrypt v.7 can also create hidden containers that are not evident to an intruder. You can simply create another (hidden) container inside an already existing (shell) container. Data stored within shell and hidden containers can be completely different, passwords for the containers are also different, and it is impossible to tell whether or not a shell container is concealing a hidden container. The help documentation of Version 7 contains detailed information on the creation and management of hidden containers.
5. In earlier versions of BestCrypt, containers were supported only in the root directory. This limitation has been removed and you can now mount containers in sub-directories from BestCrypt Control Panel. Containers can now be mounted from remote computers without mapping remote disk resources.
6. The BestCrypt Control Panel now allows the organization of containers into separate groups. Such a group may include containers located in different directories and on remote computers. The user can group containers as required. Container grouping information is specific to individual users. This adds a new level of security where computers are used by multiple users with each user being required to mount their own containers.
7. BestCrypt v.7 includes Rijndael encryption algorithm. The algorithm was invented by Joan Daemen and Vincent Rijmen, and recently NIST selected the algorithm as an Advanced Encryption Standard (AES). For more information on the algorithm, visit the Rijndael Home Page. To provide continuity and compatibility with earlier versions, BestCrypt v.7 continues to support containers created earlier with the DES algorithm. However v.7 will not create any new DES containers, as the 56-bit key of DES can no longer be considered sufficiently secure.
8. BestCrypt v.7 allows the addition of new passwords for existing containers, created with the SHA-1 Key Generator. If you wish to allow another user to mount one of your containers, you can now assign a new additional password to a container specific to an individual user. This permits you to choose which users have access to particular containers.
Requirements
Windows NT/2000/2003 Server has to be configured as Domain Controller.
tags bestcrypt corporate swap file bestcrypt software block chaining chaining mode you can the algorithm can now cipher block hidden containers the swap client computers administrating database
bestcrypt corporate swap file bestcrypt software block chaining chaining mode you can the algorithm can now cipher block hidden containers the swap client computers administrating database
Download BestCrypt Corporate 1.12
 Download BestCrypt Corporate 1.12
Download BestCrypt Corporate 1.12
Purchase:  Buy BestCrypt Corporate 1.12
Buy BestCrypt Corporate 1.12
Similar software
 BestCrypt Corporate 1.12
BestCrypt Corporate 1.12
Jetico, Inc.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
 BestCrypt 8.04 beta
BestCrypt 8.04 beta
Jetico, Inc.
BestCrypt software will create and will support encrypted virtual disks.
 BestCrypt Key 7.9
BestCrypt Key 7.9
Passware
BestCrypt Key will recover passwords for virtual hard disks encrypted with BestCrypt (.
 Idea crypting module for BestCrypt 7.20
Idea crypting module for BestCrypt 7.20
Igor Arsenin
Idea crypting driver for BestCrypt version 6.
 BestCrypt Bruteforcer/Cracker 1.0
BestCrypt Bruteforcer/Cracker 1.0
Corbio
BestCrypt Bruteforcer/Cracker is a bruteforcer for virtual disks.
 BestCrypt Volume Encryption 5.12.3
BestCrypt Volume Encryption 5.12.3
Jetico Inc.
BestCrypt Volume Encryption software will provide transparent encrypting all the data stored on removable and fixed disk devices.
 CryptoExpert 2007 Professional 7.1.1
CryptoExpert 2007 Professional 7.1.1
SecureAction Research LLC
CryptoExpert is a software which will make transparent encryption using virtual hard drives.
 CryptoExpert 2007 Lite 7.1.1
CryptoExpert 2007 Lite 7.1.1
SecureAction Research LLC
CryptoExpert Lite is a free encryption software that uses an on-the-fly encryption system to encrypt and decrypt your data.
 PrimaSoft Encryption - Service Edition 1.0
PrimaSoft Encryption - Service Edition 1.0
PrimaSoft PC Inc
PrimaSoft Encryption is a Windows program which allows you quickly and easely to run scheduled encryption and decryption sessions as a service process using the latest industry standard strong encryption algorithms: AES (US Advanced Encryption Standard, secret-key encryption also known as Rijndael); Twofish (secret-key encryption); RSA (public-key encryption)
Features:
· Encryption software: service process: You can run scheduled auto-recurring encryption and decryption sessions as a service process.
 CryptoForge 5.5.0
CryptoForge 5.5.0
Ranquel Technologies
CryptoForge is a suite of encryption tools for personal and professional security.
 BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.
BestCrypt Corporate provides protection of data in corporate networks using strong encryption algorithms.![]() bestcrypt corporate swap file bestcrypt software block chaining chaining mode you can the algorithm can now cipher block hidden containers the swap client computers administrating database
bestcrypt corporate swap file bestcrypt software block chaining chaining mode you can the algorithm can now cipher block hidden containers the swap client computers administrating database
![]() Download BestCrypt Corporate 1.12
Download BestCrypt Corporate 1.12![]() Buy BestCrypt Corporate 1.12
Buy BestCrypt Corporate 1.12
 BestCrypt Corporate 1.12
BestCrypt Corporate 1.12 BestCrypt 8.04 beta
BestCrypt 8.04 beta BestCrypt Key 7.9
BestCrypt Key 7.9 Idea crypting module for BestCrypt 7.20
Idea crypting module for BestCrypt 7.20 BestCrypt Bruteforcer/Cracker 1.0
BestCrypt Bruteforcer/Cracker 1.0 BestCrypt Volume Encryption 5.12.3
BestCrypt Volume Encryption 5.12.3 CryptoExpert 2007 Professional 7.1.1
CryptoExpert 2007 Professional 7.1.1 CryptoExpert 2007 Lite 7.1.1
CryptoExpert 2007 Lite 7.1.1 PrimaSoft Encryption - Service Edition 1.0
PrimaSoft Encryption - Service Edition 1.0 CryptoForge 5.5.0
CryptoForge 5.5.0