TrojanShield 2.20
 Use Trojan Shield to protect yourself from hackers and Trojan viruses.
Use Trojan Shield to protect yourself from hackers and Trojan viruses.
|
Use Trojan Shield to protect yourself from hackers and Trojan viruses.
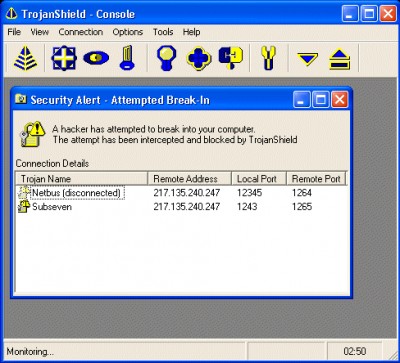
If a hacker tries to break into your computer, Trojan Shield automatically warns you so you can take action against them.
You don't need to be a computer expert to use Trojan Shield, Just install it and let it go to work.
TrojanShield features
Limitations
tags![]() your computer into your break into trojan shield process manager trojan servers trojanshield console you can allows you about the the hacker programs which startup manager
your computer into your break into trojan shield process manager trojan servers trojanshield console you can allows you about the the hacker programs which startup manager
Download TrojanShield 2.20
Purchase: ![]() Buy TrojanShield 2.20
Buy TrojanShield 2.20
Similar software
 TrojanShield 2.20
TrojanShield 2.20
TrojanShield Development
Use Trojan Shield to protect yourself from hackers and Trojan viruses.
 Anti-Hacker Expert 2003 1.6
Anti-Hacker Expert 2003 1.6
Net2Soft Inc
Anti-Hacker Expert Trojan will scan and kill trojans and hacker programs.
 Trojan Guarder Gold 7.14
Trojan Guarder Gold 7.14
Your-Soft
Trojan Guarder Gold will detect and eliminate viruses, Trojans and macro viruses, even new and unknown ones, on your computer
Trojan Guarder initates a system named Guard Ghost to supervise all running processes in memory system, Windows files and open ports to search worms and trojan horses at any time.
 Trojan Slayer 2.0.0
Trojan Slayer 2.0.0
Leithauser Research
Trojan Slayer is a tool which helps to protect your computer from Trojan infections.
 UnHackMe 4. beta 1
UnHackMe 4. beta 1
Greatis Software
UnHackMe allows you to detect and remove a new generation of Trojan programs - invisible Trojans.
 TDS-3 Professional
TDS-3 Professional
DiamondCS
First released in 1997, TDS (Trojan Defence Suite) is one of the longest established anti-trojan programs in existence and today is widely considered to be the most powerful and comprehensive anti-trojan program by the Internet security community.
 Trojan Remover 6.8.2
Trojan Remover 6.8.2
Simply Super Software
Trojan Remover was written to aid in the removal of Trojan Horses and Internet Worms when standard anti-virus software has either failed to detect the problem or is unable to effectively eliminate it.
 Trojan.Lodear Removal Tool 1.3.0
Trojan.Lodear Removal Tool 1.3.0
Symantec Corporation
Trojan.
 Look 'Trojan' Stop 2005
Look 'Trojan' Stop 2005
LoyLab
Look 'Trojan' Stop is used to scan and remove trojan horses, viruses, and spyware from your PC, and protect your PC.
 Trojan.Abwiz Removal Tool 1.0.0
Trojan.Abwiz Removal Tool 1.0.0
Symantec Corporation
Trojan.