Proteg 3.1
 Proteg is an innovative software solution that allows users to secure their personal or notebook computers by preventing unauthorized access.
Proteg is an innovative software solution that allows users to secure their personal or notebook computers by preventing unauthorized access.
|
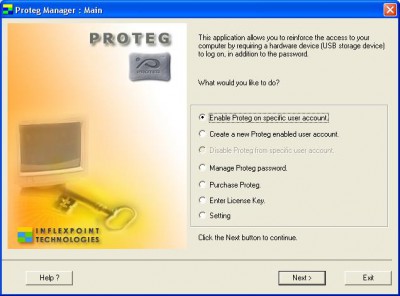
Proteg is an innovative software solution that allows users to secure their personal or notebook computers by preventing unauthorized access. It fortifies the existing Windows login mechanism by binding the user account to an ubiquitous hardware device, a portable USB storage device (USB Key, USB flash drive, thumbdrive). An additional hardware component becomes compulsory in order to login to the computer instead of relying solely on the conventional username and password pair.
Due to the increasing threats, passwords - the way most people access their computers today - can no longer keep pace with the security requirements of today’s challenging computing world. Over the years the password technique has not kept up with new technologies and methods used by hackers. One can easily gain access to the latest hacking program, many freely available over the Internet, enabling unauthorized access to valuable information resources which reside in our computer.
Unauthorized access also means invasion of our privacy. To better secure our information assets, Proteg provides a sophisticated technique for user identification and authentication to improve on passwords. This technique can certainly offer much greater security than passwords as this hardware based system (commonly known as two-factor authentication system) creates a physical link between a user and his identity.
In a two-factor authentication system like Proteg, the user is required to present the physical hardware (something the user has) and provide the correct password (something the user knows) that corresponds to the said hardware in order to gain legitimate access to the system.
Although smart cards and one-time password generator devices can be very effective in providing two-factor authentication, they are typically too expensive, difficult to manage and inflexible. Despite the enhanced level of security provided, these technologies come at high costs, much of which is due to added hardware component.
tags![]() the user unauthorized access factor authentication two factor something the authentication system over the hardware component
the user unauthorized access factor authentication two factor something the authentication system over the hardware component
Download Proteg 3.1
Purchase: ![]() Buy Proteg 3.1
Buy Proteg 3.1
Similar software
 Proteg 3.1
Proteg 3.1
Inflexpoint Technologies
Proteg is an innovative software solution that allows users to secure their personal or notebook computers by preventing unauthorized access.
 Proteg Enterprise 2005 4.7
Proteg Enterprise 2005 4.7
Inflexpoint Technologies
Proteg Enterprise 2005 is a software that allows users to secure their personal or notebook computers by preventing unauthorized access.
 Natural Login Pro 1.10
Natural Login Pro 1.10
Palcott Software
Natural Login Pro - Highly secure login without password! At last a highly secure login software for Windows designed for human beings.
 Dekart Logon for Citrix ICA Client 2.02
Dekart Logon for Citrix ICA Client 2.02
Dekart
Stop memorising logins, passwords, Citrix servers and manually entering them; store all your Citrix connections on one USB flash drive, smart card, or token; enjoy automated access - simply insert the USB drive and pass convenient identification.
 Dekart Logon 2.21
Dekart Logon 2.21
Dekart
Protect access to notebook and desktop computers running Microsot Windows 95/98/ME/NT/2000/XP.
 FaceCode v - 2.0
FaceCode v - 2.0
Recognix Technologies LTD
FaceCode - Face Recognition PC access control software
FaceCode gives you complete access control to your PC like no other product before.
 SMS Secure Access 1.00.05
SMS Secure Access 1.00.05
SMS Secure Access
SMS Secure Access is an ad-on security system for your Terminal Service environment or any system you can Script.
 TokenKey 1.8
TokenKey 1.8
DefendGate
TokenKey turns your regular USB key into an effective security token utility.
 Double Password 1.21
Double Password 1.21
Mipko Software
Want to be sure that no one except you can get easy access to your personal computer?
Simply install Double Password! This program breaks fresh ground in your computer security.
 ID Devices Lock 1.2
ID Devices Lock 1.2
ID Security Suite
ID Devices Lock is a very useful program to have on your computer in order to protect your personal information and prevent unauthorized access.